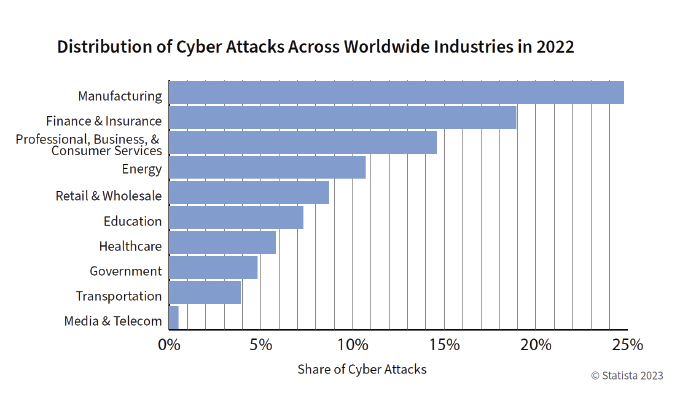
Effective cybersecurity for critical infrastructure may pose one of the most significant threats to modern society. While local, state, and national policies address threats both foreign and domestic, the ability to effectively protect against cyberattacks is severely lacking across many industries. In 2022, nearly 25 percent of all cyberattacks targeted the manufacturing sector, closely followed by the finance and consumer services industries. The pace of attacks is only increasing, with small and medium enterprises standing to lose the most due to a lack of time, expertise, or awareness of cybersecurity practices. As the most targeted nation for cyberattacks, the United States experienced 57 percent more cyberattacks in 2022 than in 2021. Globally, cyberattacks in 2022 increased 38 percent over the previous year. The result is that many small and medium enterprises—which rely heavily on technology for production—do not have a cyber protection plan that protects their critical assets.
Cybersecurity attacks can take many forms, but all intend to cause a loss in operations, wealth, or capability. At its core, cybersecurity is a balance of risk tolerance (just like investing), strategic initiatives, or recruiting. Unfortunately, in the connected landscape of modern software, it is not possible to be 100 percent secure and guarantee with complete confidence that access and data will never be compromised. On one hand, an organization could operate in a completely closed environment, with zero transfer of information to or from any system. This is not practical in most cases and would certainly lead to the company’s collapse. On the other hand, a fully open system with unfettered access to any information is not feasible, either. An appropriate balance must be struck, especially in the manufacturing sector, to foster efficient operations with secure practices.
In response to current cybersecurity threats, NCMS has partnered with public agencies such as the Cybersecurity Innovation Institute (CyManII), the Department of Homeland Security (DHS), and the National Institute of Standards and Technology (NIST), along with private sector cybersecurity stakeholders, to help identify key issues, opportunities, and mitigation solutions, as these attacks threaten the production capabilities of every connected manufacturing firm. NCMS’s Cybersecurity Strategic Initiative helps manufacturers address cybersecurity issues and convenes technical experts in operational technology and cybersecurity to help companies identify, mitigate, and close security and resilience gaps.
CURRENT CYBERSECURITY CHALLENGES
The goal of cybersecurity has become harder to reach every year. America’s critical infrastructure sectors rely on internet-connected devices and systems to deliver essential services. The astronomical increase in Internet of Things (IoT) devices, digital manufacturing initiatives, and paperless business services across all industry sectors poses a significant cybersecurity challenge.
By 2025, there will be an estimated 41.6 billion IoT devices, capable of generating an astronomical 79.4 zettabytes (ZB) of data, as forecasted by the International Data Corporation (IDC). These devices include smartphones, home security systems, health monitoring devices, autonomous vehicles, and digital control systems, to name just a few.
In an IBM-sponsored study of companies in 17 countries, the average cost of a data breach reached an all-time high of $4.35 million in 2022, and of 550 companies that reported a data breach in 2022, 83 percent experienced more than one breach. Insider threats, which are difficult to detect, account for an estimated 60 percent of cyberattacks. Most cases go unnoticed for months or even years. The remaining cyberattacks are perpetrated by organized criminals, amateurs, and professional hackers, including state-sponsored actors. The motives of cyberattacks generally fall into three categories: seeking access to data, usually for financial gain; espionage, to monitor the activities of targets; and sabotage, to seek the destruction, defamation, or blackmail of targets.
CYBERSECURITY RESOURCE: NIST
The National Institute of Standards and Technology (NIST)’s cybersecurity framework was developed to improve cybersecurity risk management for critical infrastructure, but it can be used by organizations in any sector of the economy—including companies, government agencies, and nonprofit organizations—regardless of their focus or size.
COMMON TYPES OF ATTACKS
A cyberattack of any scale can be disastrous for small and medium enterprises. Loss of access to data and information only compounds supply chain issues, cycle time efficiency, and shortages in the skilled workforce. In 2022, the average time of recovery from a cyberattack in the manufacturing sector rose to 23 business days, resulting in many affected shops closing their doors.
One recent study found that—other than IT failures, such as cloud misconfiguration—the most common data breaches were caused by:
Compromised Credentials and Phishing
In 2022, stolen or compromised credentials cost companies an average of $4.5 million. These breaches had the longest life cycle: 243 days to identify the breach, and another 84 days to contain the breach.
Phishing attempts to steal users’ credentials or sensitive data such as credit card numbers. Scammers send emails or text messages designed to look as though they’re coming from a legitimate source, using fake hyperlinks. In 2022, phishing attacks cost companies an average of $4.91 million.
Supply Chain Attacks
In 2022, an alarming 47 percent of attacks on manufacturing were caused due to vulnerabilities that victim organizations had not yet or could not patch, highlighting the need for organizations to prioritize vulnerability management.
Malware
Destructive malware—malicious software—is designed perform an unauthorized process that will adversely impact the confidentiality, integrity, or availability of an information system. Malware has the capability to render affected systems inoperable. Most malware causes destruction through the deletion of files that are critical to the operating system’s ability to run. There are many
types of malware:
- Viruses infect programs to delete files or steal information, then self-replicate.
- Zero-Day malware is unknown to current antivirus software, which forces antivirus developers to work quickly to eliminate these viruses, all while hackers are quickly programming new strains of malware.
- Worms are programs that can replicate themselves over a network without any user interaction.
- Trojan Horses appear to be useful software, or a fun game, but have malicious programs hidden inside, usually spyware and adware, which can steal usernames and passwords.
- Drive-by downloads are websites that infect users’ computers after clicking on a link. Cybercriminals use search engine optimization (SEO) to make these sites popular on search engines.
- Bots take control of computers without the user’s knowledge.
CYBERSECURITY RESOURCE: CISA
The Cybersecurity and Infrastructure Security Agency provides
the Critical Manufacturing Sector Cybersecurity Framework Implementation Guidance, which was developed to help Critical Manufacturing Sector owners and operators use the cybersecurity framework developed by the
National Institute of Standards and Technology (NIST).
Ransomware
While all types of malware can cause serious damage, the threat from ransomware has grown exponentially over the past few years. Ransomware encrypts important files and demands the user to pay a ransom to have the files unencrypted. Phishing emails are the most used for ransomware attacks. In 2021, ransomware accounted for 23 percent of attacks on manufacturing companies. The average cost of a ransomware attack was $4.54 million in 2022.
A concerning new trend in ransomware is the expansion of “triple extortion” tactics. In this type of attack, threat actors encrypt and steal data, and also threaten to engage in a distributed denial of service (DDoS) attack against the affected organization. Moreover, cybercriminals often pressure the primary victim’s business partners into paying a ransom to prevent their own data leakages or business disruptions caused by a ransomware attack.
A LOOK AHEAD
In part 2 of this series, we’ll breakdown actionable steps you can take to minimize these above-stated risks and improve your overall cybersecurity. In the expansive and increasingly digitally integrated manufacturing sector, it may be impossible to eliminate cyberattacks, but with proper preparation and committed oversite, the damage from these attacks can be greatly minimized.
FOR MORE INFORMATION
The National Center for Manufacturing Sciences (NCMS) has been working with our partners for several years to develop appropriate and cost-effective methods to protect information assets. Obtaining the appropriate level of Cybersecurity Maturity Model Certification (CMMC) is increasingly required for government contractors. For more information, www.ncms.org.
MODERN PUMPING TODAY, June 2024
Did you enjoy this article?
Subscribe to the FREE Digital Edition of Modern Pumping Today Magazine!


